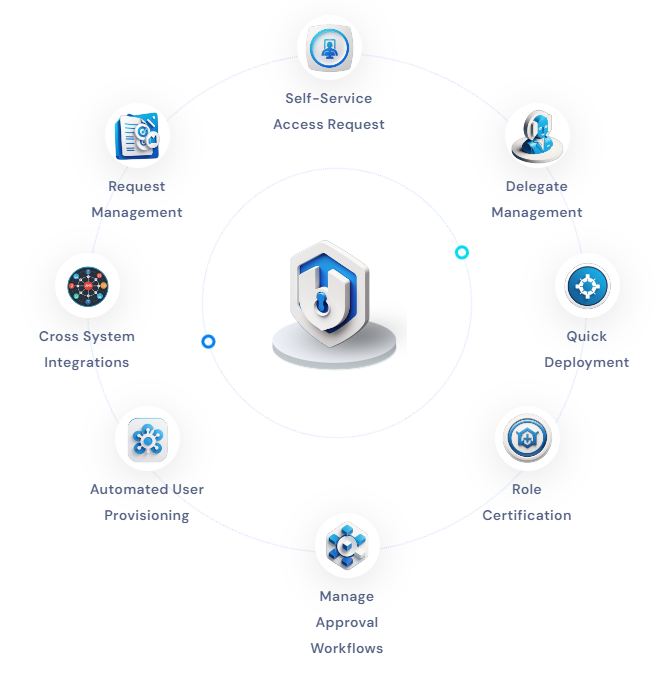
Key Features of AMS : Access management system is a term used to describe the rules, procedures, and technologies an organization uses to control and manage access to its information systems and data. This system is vital to an organization’s security strategy, ensuring only authorized individuals can access sensitive information and systems.
Access management systems commonly employ authentication and authorization processes such as passwords, biometric verification, or access control lists (ACLs) to regulate resource access. Additionally, they often include monitoring and auditing measures to detect and respond to unauthorized access attempts or suspicious activity.
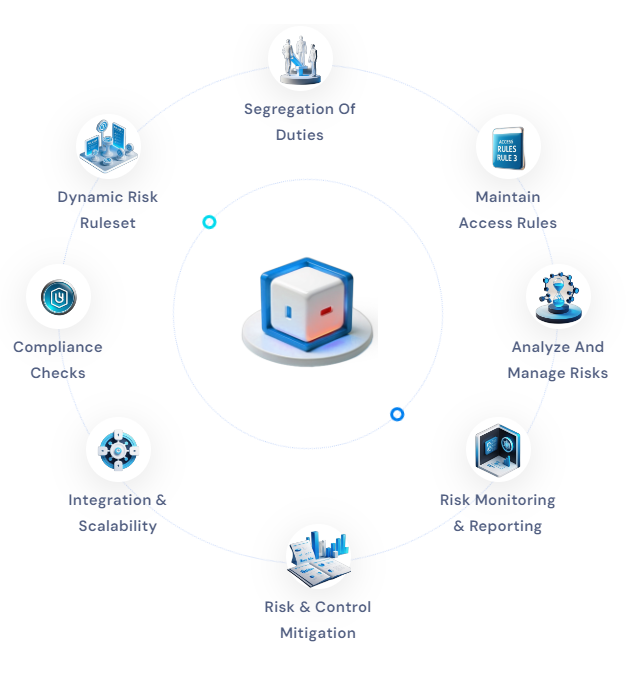
Key Features of RMS : An effective risk management system is a potent weapon in an organization’s arsenal, comprising a set of processes, tools, and techniques that enable organizations to identify, assess, and manage risks that could impact their objectives. Its primary aim is to minimize adverse consequences and maximize growth opportunities.
Organizations can make informed decisions based on a comprehensive understanding of potential risks by identifying potential risks, analyzing their likelihood and impact, and developing strategies to manage or mitigate them. This proactive approach empowers organizations to be confident and prepared for unforeseen events, paving the way for a successful future.
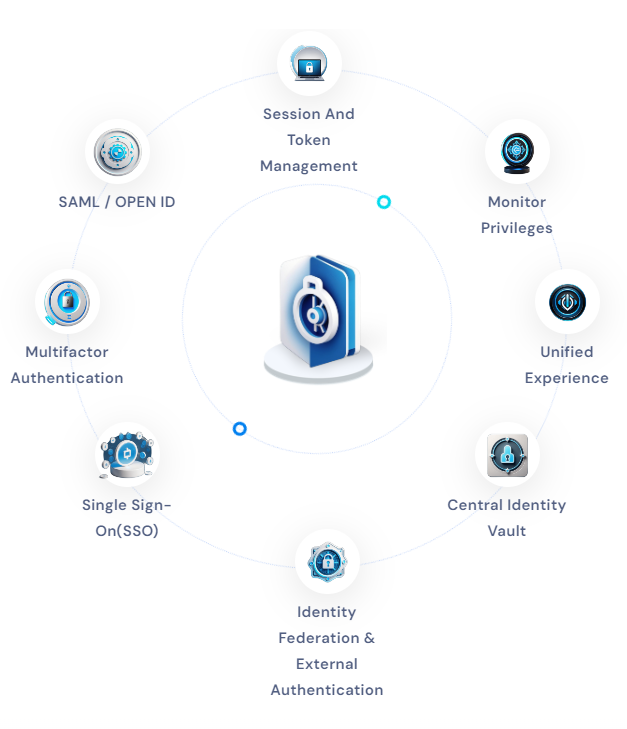
Key Features of IMS : Identity Management System (IMS) is a comprehensive framework designed to manage digital identities, encompassing user authentication, authorization, and access control. It is a centralized system for managing user identities and accessing various resources and services, such as applications, databases, and networks.
IMS typically includes advanced features such as single sign-on, identity synchronization, password management, and multi-factor authentication. Large organizations commonly employ it to streamline the complex and time-consuming process of managing user identities and resource access.
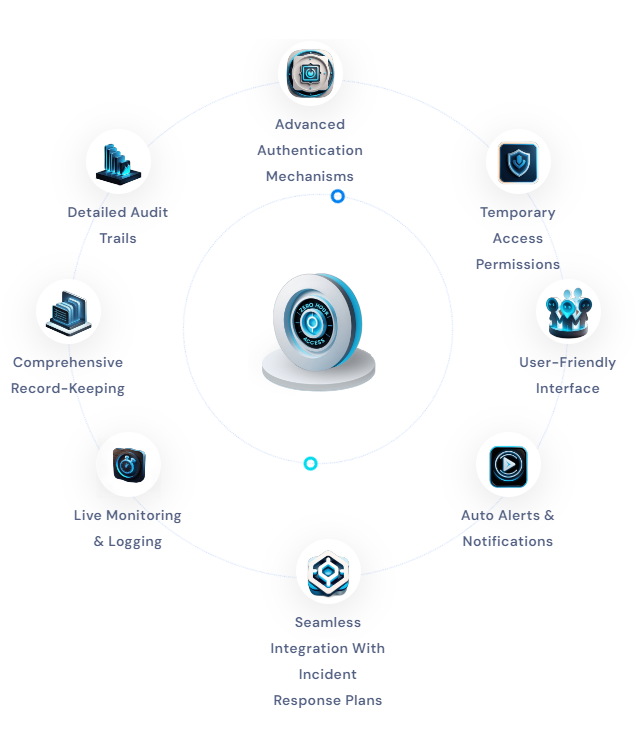
What is Z-AMS?: Zero-Hour Access Management (Z-AMS) plays a crucial role in our cybersecurity strategy by providing a comprehensive framework for managing access to vital systems and data during emergencies.
This proactive approach ensures that authorized personnel have the necessary access rights to swiftly address urgent issues while maintaining the security and integrity of sensitive information.
By effectively mitigating risks and supporting business continuity, Z-AMS is key to safeguarding our organization against potential security threats.