- /
- Services
- /
- GRC and Cybersecurity
- /
- Cybersecurity, Data Protection and...
- /
- SAP Enterprise Threat Detection

SAP Enterprise Threat Detection is an integrated solution designed to help organizations Simplify, Automate and Monitor User access management.
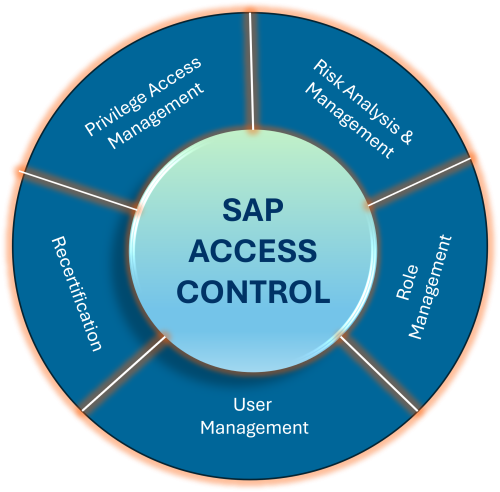
Our team of experts offers comprehensive support for SAP Cloud Identity Access Governance (AC), including:
We also help implementing the entire SAP GRC suite, including SAP Access Control (AC), SAP Process Control (PC), SAP Risk Management (RM), SAP Audit Management (AM) and SAP Business Integrity (BIS) Screening. These integrated solutions will enhance your organization’s ability to manage risks, ensure compliance, and optimize overall performance.
Interested in learning more about SAP Cloud Identity Access Governance or purchasing the solution for your organization?
Our sales team is ready to assist you with any inquiries, provide detailed product information, and offer tailored solutions to meet your organization’s risk management needs. We look forward to helping you enhance your risk management capabilities with SAP Cloud Identity Access Governance.