SAP Security
Application Security
Security design is the key to the business success, it should be simple, easily maintainable and flexible for the future organizational needs
Our SAP certified security experts work with you to understand your business requirements to plan, design and develop ahead of your implementation to ensure right security is in place to minimize your application vulnerabilities
Our Application security design goal is always to simplify, standardize and automate where ever possible
We ensure your applications comply with necessary regulations and help your organization to follow application security best practices
We’ll help you with all the necessary actions to remediate the identified risks by Access and Audit reviews
We have the expertise for any SAP productions out there in the market, for example: SAP ECC, S/4 HANA, HANA , GRC, BW, APO, HCM, GTS,SCM, BOBJ, Ariba, Hybris, Success Factors, Solution Manger , PI/PO, SLT ..etc
SAP HANA Security
You need to meet the ever increasing cyber-security challenges, keep your systems secure, and stay on top of the compliance and regulatory requirements of today’s digital world. You can run and operate SAP HANA securely in diverse environments, implementing your specific compliance, security, and regulatory requirements.
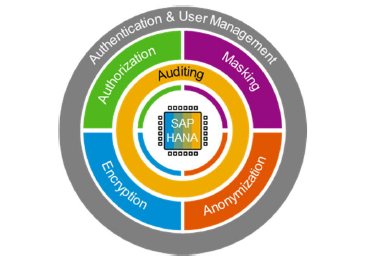
Our SAP Security team is one of the few globally who have SAP HANA expertise with multiple implementations experience, we’ll help you with
- Design, Develop, Test and Implement HANA DB Security using Repository roles
- User and Role management in single and multitenant HANA environments
- Develop HDI-based roles in HANA XSA environment
- Securing data using Classic, SQL or Dynamic Analytical Privileges
- Automate user access in HANA based on the authorizations of the user in the transactional system for example: SAP ERP, SAP BW..etc
- Develop SQL repository procedures to automate user management and reporting
- Data Masking and Anonymization
- XS Classic and XSA Security
- Authentication and SSO using SAML, Kerberos ..etc
- Integrate HANA with SLT, SDI (Smart Data Integration), SDA (Smart Data Access)…etc
- Integrate HANA with Tableau, BOBJ, Lumira..etc reporting applications
- Configure and enable auditing
- Configure security and password parameters
SAP Governance, Risk and Compliance (GRC)
SAP GRC Access control and Process control are automated tools to manage an internal security model, remediate compliance issues, improve efficiency and monitor potential business risks within an SAP system.
Mindfore helps customers with
- SAP GRC Solution (Access Control and Process Control) - Implementation, Migration, Technical upgrade, Support and any client-specific needs
- SAP GRC Rule set review and updates for versions 10.x, 5.x..etc
- GRC Risk review (SoD and Sensitive access), remediate and mitigate
- GRC Implementation Review, Optimization and Roadmap Development
- GRC Business Process Controls Design, implement and Evaluation
SAP Identity Management (IdM)
Embed identity management into your business processes – for tighter IT security
Reduce risk and centrally manage user access across your enterprise – with SAP Identity Management. The software integrates with your business processes to provide robust data and application security. Keep your operations running smoothly, reduce costs – and boost productivity by providing role-based user access, self-service password reset, approval workflows, and more.
Our Certified SAP IdM consultants help customers successfully design, implement and support SAP IdM
Cyber Security
The threat of cyber-attack is one of the greatest risks organizations are facing today. The volume and sophistication of threats has increased exponentially and has led to a wave of data breaches involving the theft of customer information and intellectual property.
Assess
We’ll initially perform a full vulnerability assessment of your system software which includes the standard and custom code scans, security patch reviews ..etc to identify system vulnerabilities
Remediate
We’ll help you remediate the code and system vulnerabilities based holistic analysis of transaction and assessment reports.
Prevent
We help you monitor and prevent unauthorized critical system changes to prevent ERP systems from becoming insecure or non-compliant while continuously assuring configurations adhere to corporate policies for all SAP versions, including S/4 HANA